12 KiB
| title | description |
|---|---|
| Routing & Load Balancing Overview |Traefik Docs | Read the official Traefik documentation to learn more on the Traefik Proxy architecture and the components that enable the routes to be created. |
Overview
What's Happening to the Requests? {: .subtitle }
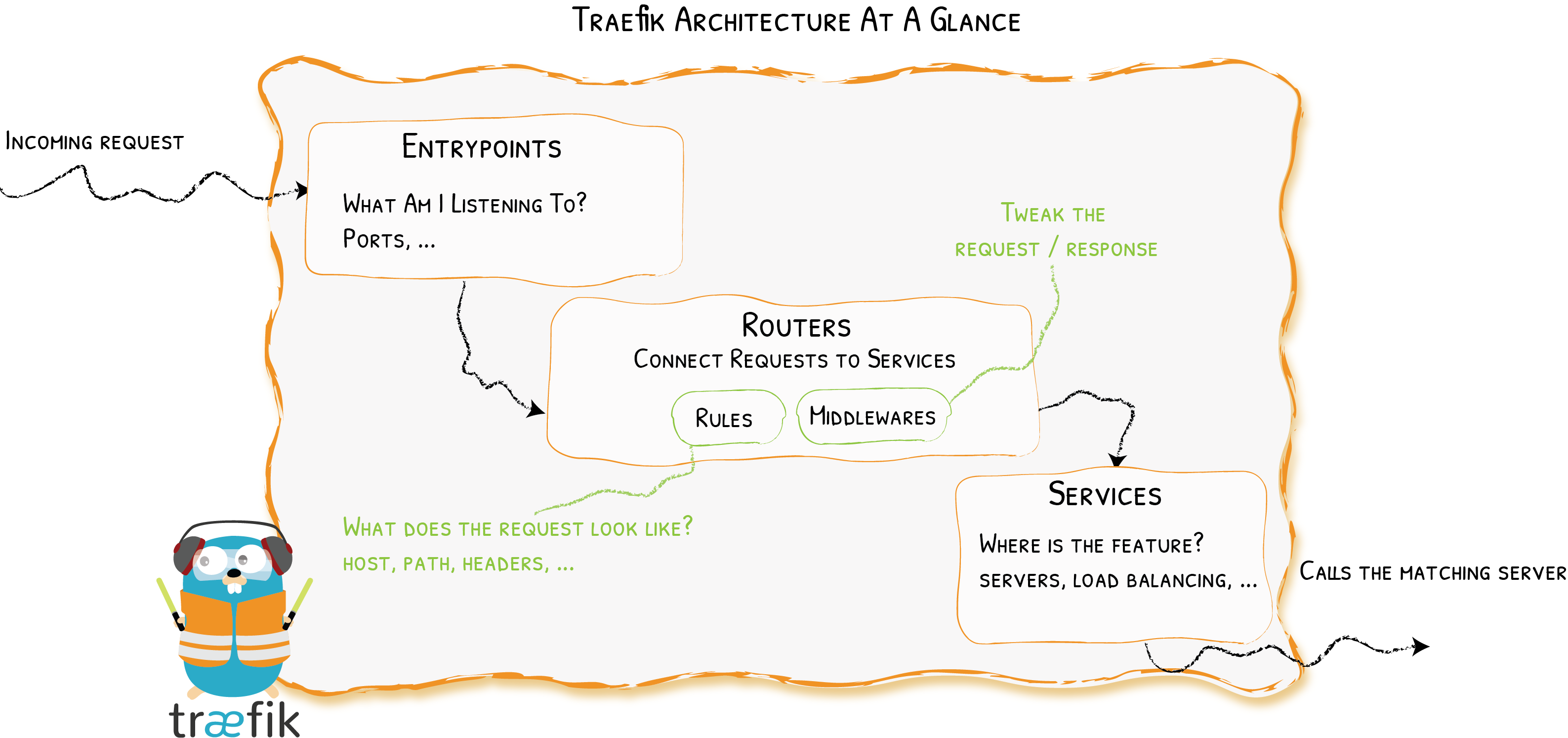
Let's zoom in on Traefik's architecture and talk about the components that enable the routes to be created.
First, when you start Traefik, you define entrypoints (in their most basic forms, they are port numbers). Then, connected to these entrypoints, routers analyze the incoming requests to see if they match a set of rules. If they do, the router might transform the request using pieces of middleware before forwarding them to your services.
Clear Responsibilities
- Providers discover the services that live on your infrastructure (their IP, health, ...)
- Entrypoints listen for incoming traffic (ports, ...)
- Routers analyse the requests (host, path, headers, SSL, ...)
- Services forward the request to your services (load balancing, ...)
- Middlewares may update the request or make decisions based on the request (authentication, rate limiting, headers, ...)
Example with a File Provider
Below is an example of a full configuration file for the file provider that forwards http://example.com/whoami/ requests to a service reachable on http://private/whoami-service/.
In the process, Traefik will make sure that the user is authenticated (using the BasicAuth middleware).
Static configuration:
entryPoints:
web:
# Listen on port 8081 for incoming requests
address: :8081
providers:
# Enable the file provider to define routers / middlewares / services in file
file:
directory: /path/to/dynamic/conf
[entryPoints]
[entryPoints.web]
# Listen on port 8081 for incoming requests
address = ":8081"
[providers]
# Enable the file provider to define routers / middlewares / services in file
[providers.file]
directory = "/path/to/dynamic/conf"
# Listen on port 8081 for incoming requests
--entryPoints.web.address=:8081
# Enable the file provider to define routers / middlewares / services in file
--providers.file.directory=/path/to/dynamic/conf
Dynamic configuration:
# http routing section
http:
routers:
# Define a connection between requests and services
to-whoami:
rule: "Host(`example.com`) && PathPrefix(`/whoami/`)"
# If the rule matches, applies the middleware
middlewares:
- test-user
# If the rule matches, forward to the whoami service (declared below)
service: whoami
middlewares:
# Define an authentication mechanism
test-user:
basicAuth:
users:
- test:$apr1$H6uskkkW$IgXLP6ewTrSuBkTrqE8wj/
services:
# Define how to reach an existing service on our infrastructure
whoami:
loadBalancer:
servers:
- url: http://private/whoami-service
# http routing section
[http]
[http.routers]
# Define a connection between requests and services
[http.routers.to-whoami]
rule = "Host(`example.com`) && PathPrefix(`/whoami/`)"
# If the rule matches, applies the middleware
middlewares = ["test-user"]
# If the rule matches, forward to the whoami service (declared below)
service = "whoami"
[http.middlewares]
# Define an authentication mechanism
[http.middlewares.test-user.basicAuth]
users = ["test:$apr1$H6uskkkW$IgXLP6ewTrSuBkTrqE8wj/"]
[http.services]
# Define how to reach an existing service on our infrastructure
[http.services.whoami.loadBalancer]
[[http.services.whoami.loadBalancer.servers]]
url = "http://private/whoami-service"
!!! info ""
In this example, we use the [file provider](../providers/file.md).
Even if it is one of the least magical way of configuring Traefik, it explicitly describes every available notion.
!!! info "HTTP / TCP"
In this example, we've defined routing rules for http requests only.
Traefik also supports TCP requests. To add [TCP routers](./routers/index.md) and [TCP services](./services/index.md), declare them in a TCP section like in the following.
??? example "Adding a TCP route for TLS requests on whoami-tcp.example.com"
**Static Configuration**
```yaml tab="File (YAML)"
entryPoints:
web:
# Listen on port 8081 for incoming requests
address: :8081
providers:
# Enable the file provider to define routers / middlewares / services in file
file:
directory: /path/to/dynamic/conf
```
```toml tab="File (TOML)"
[entryPoints]
[entryPoints.web]
# Listen on port 8081 for incoming requests
address = ":8081"
[providers]
# Enable the file provider to define routers / middlewares / services in file
[providers.file]
directory = "/path/to/dynamic/conf"
```
```bash tab="CLI"
# Listen on port 8081 for incoming requests
--entryPoints.web.address=:8081
# Enable the file provider to define routers / middlewares / services in file
--providers.file.directory=/path/to/dynamic/conf
```
**Dynamic Configuration**
```yaml tab="YAML"
# http routing section
http:
routers:
# Define a connection between requests and services
to-whoami:
rule: Host(`example.com`) && PathPrefix(`/whoami/`)
# If the rule matches, applies the middleware
middlewares:
- test-user
# If the rule matches, forward to the whoami service (declared below)
service: whoami
middlewares:
# Define an authentication mechanism
test-user:
basicAuth:
users:
- test:$apr1$H6uskkkW$IgXLP6ewTrSuBkTrqE8wj/
services:
# Define how to reach an existing service on our infrastructure
whoami:
loadBalancer:
servers:
- url: http://private/whoami-service
tcp:
routers:
to-whoami-tcp:
service: whoami-tcp
rule: HostSNI(`whoami-tcp.example.com`)
tls: {}
services:
whoami-tcp:
loadBalancer:
servers:
- address: xx.xx.xx.xx:xx
```
```toml tab="TOML"
# http routing section
[http]
[http.routers]
# Define a connection between requests and services
[http.routers.to-whoami]
rule = "Host(`example.com`) && PathPrefix(`/whoami/`)"
# If the rule matches, applies the middleware
middlewares = ["test-user"]
# If the rule matches, forward to the whoami service (declared below)
service = "whoami"
[http.middlewares]
# Define an authentication mechanism
[http.middlewares.test-user.basicAuth]
users = ["test:$apr1$H6uskkkW$IgXLP6ewTrSuBkTrqE8wj/"]
[http.services]
# Define how to reach an existing service on our infrastructure
[http.services.whoami.loadBalancer]
[[http.services.whoami.loadBalancer.servers]]
url = "http://private/whoami-service"
[tcp]
[tcp.routers]
[tcp.routers.to-whoami-tcp]
rule = "HostSNI(`whoami-tcp.example.com`)"
service = "whoami-tcp"
[tcp.routers.to-whoami-tcp.tls]
[tcp.services]
[tcp.services.whoami-tcp.loadBalancer]
[[tcp.services.whoami-tcp.loadBalancer.servers]]
address = "xx.xx.xx.xx:xx"
```
Transport configuration
Most of what happens to the connection between the clients and Traefik, and then between Traefik and the backend servers, is configured through the entrypoints and the routers.
In addition, a few parameters are dedicated to configuring globally
what happens with the connections between Traefik and the backends.
This is done through the serversTransport section of the configuration,
which features these options:
insecureSkipVerify
Optional, Default=false
insecureSkipVerify disables SSL certificate verification.
## Static configuration
serversTransport:
insecureSkipVerify: true
## Static configuration
[serversTransport]
insecureSkipVerify = true
## Static configuration
--serversTransport.insecureSkipVerify=true
rootCAs
Optional
rootCAs is the list of certificates (as file paths, or data bytes)
that will be set as Root Certificate Authorities when using a self-signed TLS certificate.
## Static configuration
serversTransport:
rootCAs:
- foo.crt
- bar.crt
## Static configuration
[serversTransport]
rootCAs = ["foo.crt", "bar.crt"]
## Static configuration
--serversTransport.rootCAs=foo.crt,bar.crt
maxIdleConnsPerHost
Optional, Default=2
If non-zero, maxIdleConnsPerHost controls the maximum idle (keep-alive) connections to keep per-host.
## Static configuration
serversTransport:
maxIdleConnsPerHost: 7
## Static configuration
[serversTransport]
maxIdleConnsPerHost = 7
## Static configuration
--serversTransport.maxIdleConnsPerHost=7
forwardingTimeouts
forwardingTimeouts is about a number of timeouts relevant to when forwarding requests to the backend servers.
forwardingTimeouts.dialTimeout
Optional, Default=30s
dialTimeout is the maximum duration allowed for a connection to a backend server to be established.
Zero means no timeout.
## Static configuration
serversTransport:
forwardingTimeouts:
dialTimeout: 1s
## Static configuration
[serversTransport.forwardingTimeouts]
dialTimeout = "1s"
## Static configuration
--serversTransport.forwardingTimeouts.dialTimeout=1s
forwardingTimeouts.responseHeaderTimeout
Optional, Default=0s
responseHeaderTimeout, if non-zero, specifies the amount of time to wait for a server's response headers
after fully writing the request (including its body, if any).
This time does not include the time to read the response body.
Zero means no timeout.
## Static configuration
serversTransport:
forwardingTimeouts:
responseHeaderTimeout: 1s
## Static configuration
[serversTransport.forwardingTimeouts]
responseHeaderTimeout = "1s"
## Static configuration
--serversTransport.forwardingTimeouts.responseHeaderTimeout=1s
forwardingTimeouts.idleConnTimeout
Optional, Default=90s
idleConnTimeout, is the maximum amount of time an idle (keep-alive) connection
will remain idle before closing itself.
Zero means no limit.
## Static configuration
serversTransport:
forwardingTimeouts:
idleConnTimeout: 1s
## Static configuration
[serversTransport.forwardingTimeouts]
idleConnTimeout = "1s"
## Static configuration
--serversTransport.forwardingTimeouts.idleConnTimeout=1s
{!traefik-for-business-applications.md!}