- ADD TI to check the new behaviour with onHostRule and provided certificates - ADD TU on the getProvidedCertificate method |
||
|---|---|---|
| .github | ||
| .semaphoreci | ||
| .travis | ||
| acme | ||
| autogen | ||
| cluster | ||
| cmd/traefik | ||
| contrib/systemd | ||
| docs | ||
| examples | ||
| healthcheck | ||
| integration | ||
| job | ||
| log | ||
| middlewares | ||
| mocks | ||
| provider | ||
| safe | ||
| script | ||
| server | ||
| templates | ||
| testhelpers | ||
| types | ||
| vendor | ||
| version | ||
| webui | ||
| .dockerignore | ||
| .gitignore | ||
| .pre-commit-config.yaml | ||
| .travis.yml | ||
| build.Dockerfile | ||
| CHANGELOG.md | ||
| CODE_OF_CONDUCT.md | ||
| Dockerfile | ||
| generate.go | ||
| glide.lock | ||
| glide.yaml | ||
| LICENSE.md | ||
| Makefile | ||
| mkdocs.yml | ||
| README.md | ||
| requirements.txt | ||
| traefik.sample.toml | ||

Træfik (pronounced like traffic) is a modern HTTP reverse proxy and load balancer made to deploy microservices with ease. It supports several backends (Docker, Swarm, Kubernetes, Marathon, Mesos, Consul, Etcd, Zookeeper, BoltDB, Eureka, Amazon DynamoDB, Rest API, file...) to manage its configuration automatically and dynamically.
Overview
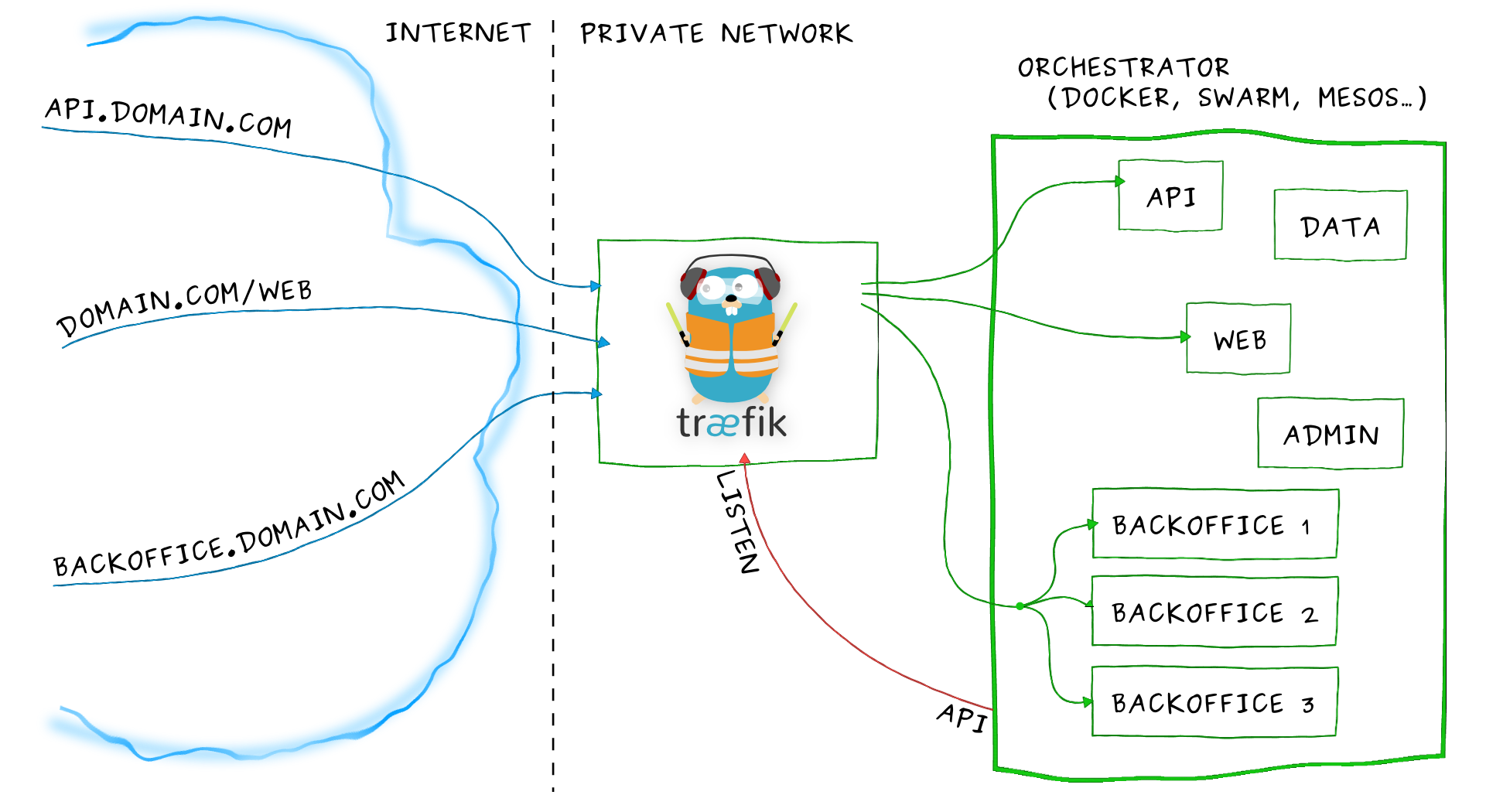
Imagine that you have deployed a bunch of microservices on your infrastructure. You probably used a service registry (like etcd or consul) and/or an orchestrator (swarm, Mesos/Marathon) to manage all these services. If you want your users to access some of your microservices from the Internet, you will have to use a reverse proxy and configure it using virtual hosts or prefix paths:
- domain
api.domain.comwill point the microserviceapiin your private network - path
domain.com/webwill point the microservicewebin your private network - domain
backoffice.domain.comwill point the microservicesbackofficein your private network, load-balancing between your multiple instances
But a microservices architecture is dynamic... Services are added, removed, killed or upgraded often, eventually several times a day.
Traditional reverse-proxies are not natively dynamic. You can't change their configuration and hot-reload easily.
Here enters Træfik.
Træfik can listen to your service registry/orchestrator API, and knows each time a microservice is added, removed, killed or upgraded, and can generate its configuration automatically. Routes to your services will be created instantly.
Run it and forget it!
Features
- It's fast
- No dependency hell, single binary made with go
- Rest API
- Multiple backends supported: Docker, Swarm, Kubernetes, Marathon, Mesos, Consul, Etcd, and more to come
- Watchers for backends, can listen for changes in backends to apply a new configuration automatically
- Hot-reloading of configuration. No need to restart the process
- Graceful shutdown http connections
- Circuit breakers on backends
- Round Robin, rebalancer load-balancers
- Rest Metrics
- Tiny official docker image included
- SSL backends support
- SSL frontend support (with SNI)
- Clean AngularJS Web UI
- Websocket support
- HTTP/2 support
- Retry request if network error
- Let's Encrypt support (Automatic HTTPS with renewal)
- High Availability with cluster mode
Quickstart
You can have a quick look at Træfik in this Katacoda tutorial that shows how to load balance requests between multiple Docker containers.
Here is a talk given by Ed Robinson at the ContainerCamp UK conference. You will learn fundamental Træfik features and see some demos with Kubernetes.
Here is a talk (in French) given by Emile Vauge at the Devoxx France 2016 conference. You will learn fundamental Træfik features and see some demos with Docker, Mesos/Marathon and Let's Encrypt.
Web UI
You can access the simple HTML frontend of Træfik.
Plumbing
- Oxy: an awesome proxy library made by Mailgun guys
- Gorilla mux: famous request router
- Negroni: web middlewares made simple
- Lego: the best Let's Encrypt library in go
Test it
- The simple way: grab the latest binary from the releases page and just run it with the sample configuration file:
./traefik --configFile=traefik.toml
- Use the tiny Docker image:
docker run -d -p 8080:8080 -p 80:80 -v $PWD/traefik.toml:/etc/traefik/traefik.toml traefik
- From sources:
git clone https://github.com/containous/traefik
Documentation
You can find the complete documentation here.
Contributing
Please refer to this section.
Code Of Conduct
Please note that this project is released with a Contributor Code of Conduct. By participating in this project you agree to abide by its terms.
Support
You can join 
Maintainers
- Emile Vauge @emilevauge
- Vincent Demeester @vdemeester
- Russell Clare @Russell-IO
- Ed Robinson @errm
- Daniel Tomcej @dtomcej
- Manuel Laufenberg @SantoDE
- Thomas Recloux @trecloux
- Timo Reimann @timoreimann
Credits
Kudos to Peka for his awesome work on the logo ![]() .
Traefik's logo licensed under the Creative Commons 3.0 Attributions license.
.
Traefik's logo licensed under the Creative Commons 3.0 Attributions license.
Traefik's logo was inspired by the gopher stickers made by Takuya Ueda (https://twitter.com/tenntenn). The original Go gopher was designed by Renee French (http://reneefrench.blogspot.com/).